In a significant counter-intelligence operation, the Gujarat Anti-Terrorist Squad (ATS) has dismantled a sophisticated cross-state espionage network orchestrated by Pakistan-based intelligence officers. The ring relied on digital deception, social engineering, and surveillance malware to target Indian military personnel and extract sensitive information.
How the Spy Network Operated
The investigation, which culminated on Thursday, revealed a meticulously planned operation. Officers from Pakistan's intelligence setup (PIOs) created a web of fake online profiles, posing as Indians to befriend potential targets. Their goal was to build trust and coax individuals into sharing classified military details.
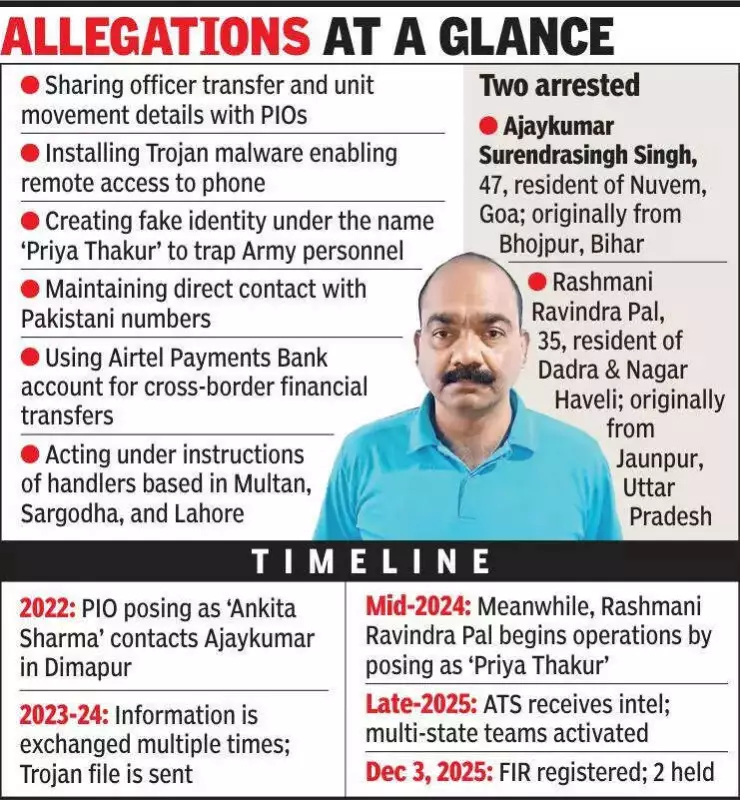
A retired Army subedar, Ajaykumar Surendrasingh Singh, was among those ensnared. During his posting in Dimapur in 2022, he was contacted by a handler using the fake identity "Ankita Sharma." Over time, the handler began eliciting information on unit deployments, officer postings, and movement patterns. In a critical escalation, the PIO also sent a Trojan malware file designed to grant remote access to the subedar's phone.
ATS Investigation Traces Links to Pakistan
The operation came to light after ATS analysts, under SP K Siddharth, flagged unusual digital communication patterns and financial transactions. A specialized cell was formed to probe the activity, which matched suspicious social media interactions with unexplained money flows.
A major breakthrough occurred when the WhatsApp profile "Ankita Sharma" was found repeatedly calling a Goa-based number. Technical analysis showed the associated IP addresses shifting between Multan and Sargodha in Pakistan. Simultaneously, financial scrutiny uncovered small, recurring transactions to an Airtel Payments Bank account.
The trail led investigators to Rashmani Ravindra Pal, a resident of Daman. She allegedly acted as a conduit for PIOs identified as "Abdul Sattar" and "Khalid." Pal created a fake profile named "Priya Thakur" to approach Army personnel selected by the handlers. She received lists of target mobile numbers from her Pakistani contacts and used the bank account to receive and transfer funds under their direction.
Evidence and Nationwide Coordination
Searches conducted by the ATS led to the recovery of crucial evidence, including:
- WhatsApp call logs from international numbers.
- Digital documents and financial records.
- Lists of mobile numbers supplied by the Pakistani handlers.
IP verification conclusively linked several communications to Multan, Sargodha, and Lahore in Pakistan. The ATS coordinated with police forces in Uttar Pradesh, Goa, and Daman to verify local links. This consolidated effort established a structured network with defined roles.
The ATS has registered an FIR under Sections 61 and 148 of the Bharatiya Nyaya Sanhita (BNS). Officers confirmed that the roles of additional individuals associated with this espionage ring are under active investigation. The case highlights the evolving threat of digital espionage and the use of social engineering by foreign agencies.